Buscar este blog
Yet another security blog with random() shit done by yet another guy in the infosec industry based in Mexico.
Entradas
Mostrando entradas de 2010
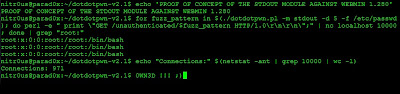
DotDotPwn v2.1 - The Traversal Directory Fuzzer
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
DotDotPwn - The Directory Traversal Fuzzer
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
Chatsubo [(in)Security Dark] Labs say Hi !
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
Advanced Persistent Threat
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
John the Ripper benchmark
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
Having fun with RISK management equations
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
NY Times - Bombing Suspect's Long Path to Times Square
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
2600 m33ting @ Toronto, Canada
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
Trend Micro Data Loss Prevention 5.2 (formerly LeakProof) Data Leakage
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
I'm a GPEN now ! ;)
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
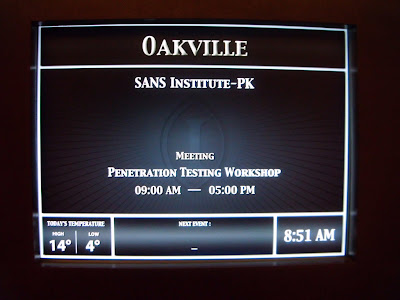
SANS Toronto - I got the Flag in the CTF ! ;)
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
c155p... my next challenge ! 4 phun & pr0fit
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
XOR Swap Algorithm
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
31337 order at Cinépolis
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
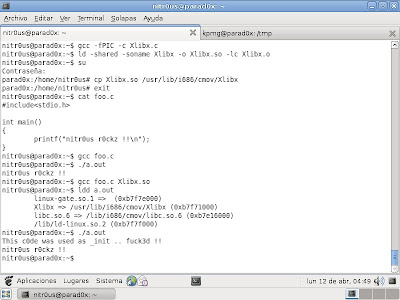
Exploiting apps replacing _init through shared libraries
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
From Hacker to C-Level
- Obtener enlace
- Correo electrónico
- Otras aplicaciones
Welcome
- Obtener enlace
- Correo electrónico
- Otras aplicaciones